Adopt an information security standard


With the ever-evolving IT landscape there is constant need for the organisations to keep a check on the security controls implemented. A huge number of cyberattacks happen every day exploiting various vulnerabilities and weaknesses within an organisations IT landscape. The security controls that worked for your organization yesterday may no longer be sufficient today. So, the organizations need to continuously evaluate and benchmark their security controls to protect their critical Infrastructure.
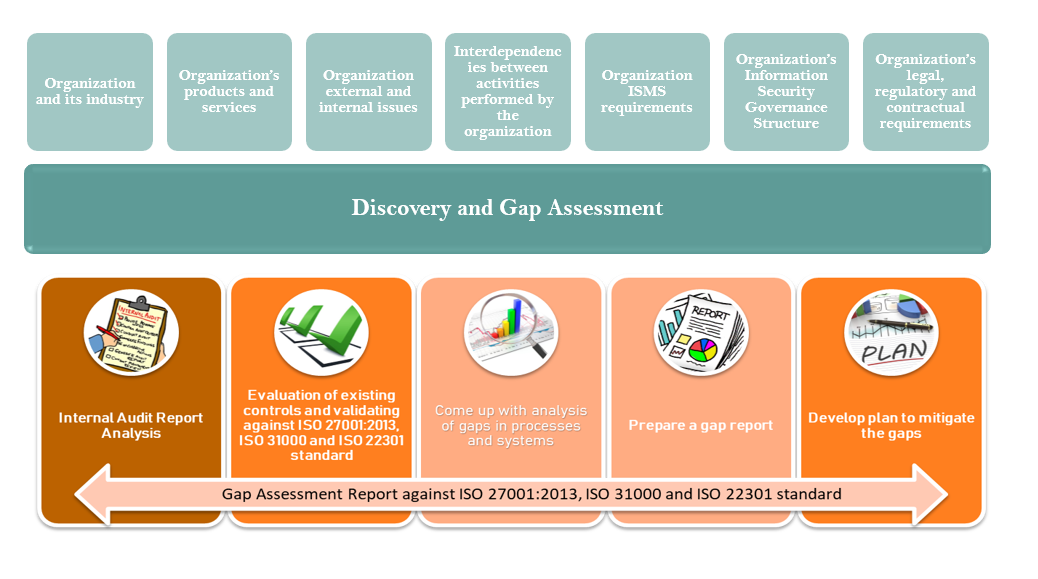
A cybersecurity gap analysis helps organizations to identify the weaknesses within their network and IT system security controls to ensure that they are suitable and effective. The cybersecurity gap analysis highlightsthe gaps that needs to bebridged by comparing organisations current practices against the best practices suitable for their threat landscape.
Following are the key steps undertaken during a Cybersecurity Gap Analysis:
Adopt an information security standard
Evaluate People and Processes
Data Gathering and Analysis
GAP Analysis